Summary
In cybersecurity, identifying and exploiting weak authentication mechanisms is a critical skill for both attackers and defenders. The Login Brute Forcing module explores the art and science of cracking passwords through systematic trial and error.
The module explores various attack vectors, from basic HTTP authentication to commonly found web login forms and remote services like SSH and FTP. You'll learn how to leverage powerful tools like Hydra and Medusa to automate the brute-forcing process, efficiently testing vast numbers of credential combinations.
By the end of this module, you'll have a deep understanding of the mechanics of brute-force attacks, the tools and techniques employed by attackers, and the strategies for defending against such threats. Whether you're a penetration tester assessing system vulnerabilities or a security professional fortifying authentication practices, the knowledge gained in this module will prove invaluable in the ongoing battle for cybersecurity.
Key topics covered in this module include:
The Fundamentals of Brute Forcing: Understanding the core principles, types, and the role of brute forcing in penetration testing.Password Security: The importance of strong passwords, common weaknesses, and the role of password policies.The Perils of Default Credentials: The dangers of default usernames and passwords and their exploitation in brute-force attacks.Brute-Forcing in Action: Practical examples of brute-forcing PINs, HTTP authentication, and web login forms using tools like Hydra and Medusa.The Power of Wordlists: The significance of dictionary attacks, building custom wordlists, and leveraging tools like CUPP for password profiling.Targeting Remote Services: Brute-forcing SSH and FTP services, highlighting their vulnerabilities and the importance of secure configurations.
This module is broken down into sections with accompanying hands-on exercises to practice each of the tactics and techniques we cover. The module ends with a practical hands-on skills assessment to gauge your understanding of the various topic areas.
As you work through the module, you will see example commands and command output for the various topics introduced. It is worth reproducing as many of these examples as possible to reinforce further the concepts introduced in each section. You can do this in the Pwnbox provided in the interactive sections, Windows machines in a lab environment as directed, or your own virtual machine.
You can start and stop the module at any time and pick up where you left off. There is no time limit or "grading," but you must complete all of the exercises and the skills assessment to receive the maximum number of cubes and have this module marked as complete in any paths you have chosen.
The module is classified as "Easy" but assumes a working knowledge of the Linux command line and an understanding of information security fundamentals.
A firm grasp of the following modules can be considered prerequisites for successful completion of this module:
- Introduction to Networking
- Linux Fundamentals
- Web Requests
Introduction
Keys and passwords, the modern equivalent of locks and combinations, secure the digital world. But what if someone tries every possible combination until they find the one that opens the door? That, in essence, is brute forcing.
What is Brute Forcing?
In cybersecurity, brute forcing is a trial-and-error method used to crack passwords, login credentials, or encryption keys. It involves systematically trying every possible combination of characters until the correct one is found. The process can be likened to a thief trying every key on a giant keyring until they find the one that unlocks the treasure chest.
The success of a brute force attack depends on several factors, including:
- The
complexityof the password or key. Longer passwords with a mix of uppercase and lowercase letters, numbers, and symbols are exponentially more complex to crack. - The
computational poweravailable to the attacker. Modern computers and specialized hardware can try billions of combinations per second, significantly reducing the time needed for a successful attack. - The
security measuresin place. Account lockouts, CAPTCHAs, and other defenses can slow down or even thwart brute-force attempts.
How Brute Forcing Works
The brute force process can be visualized as follows:
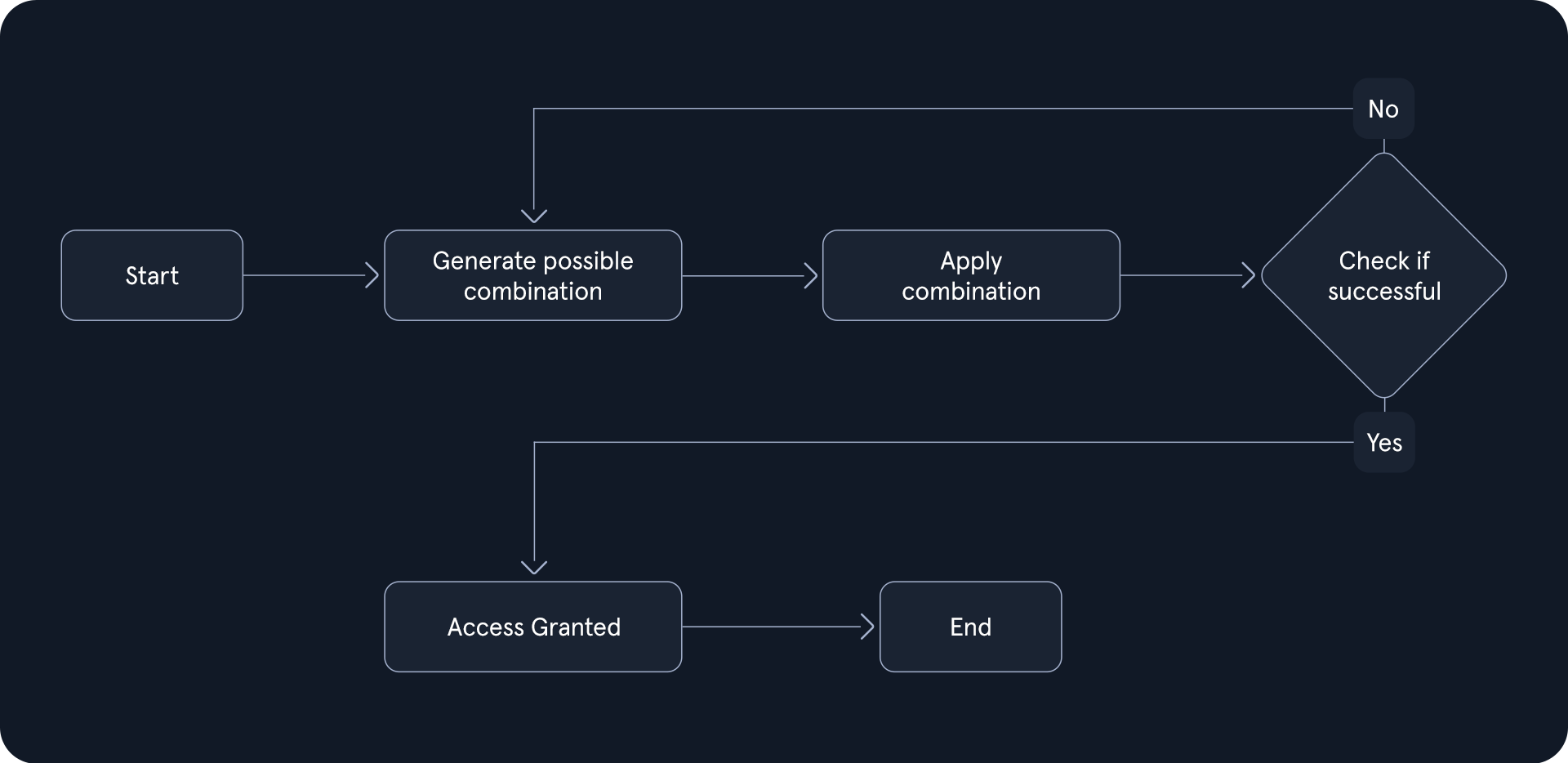
Start: The attacker initiates the brute force process, often with the aid of specialized software.Generate Possible Combination: The software generates a potential password or key combination based on predefined parameters, such as character sets and length.Apply Combination: The generated combination is attempted against the target system, such as a login form or encrypted file.Check if Successful: The system evaluates the attempted combination. If it matches the stored password or key, access is granted. Otherwise, the process continues.Access Granted: The attacker gains unauthorized access to the system or data.End: The process repeats, generating and testing new combinations until either the correct one is found or the attacker gives up.
Types of Brute Forcing
Brute forcing is not a monolithic entity but a collection of diverse techniques, each with its strengths, weaknesses, and ideal use cases. Understanding these variations is crucial for both attackers and defenders, as it enables the former to choose the most effective approach and the latter to implement targeted countermeasures. The following table provides a comparative overview of various brute-forcing methods:
| Method | Description | Example | Best Used When... |
|---|---|---|---|
Simple Brute Force |
Systematically tries all possible combinations of characters within a defined character set and length range. | Trying all combinations of lowercase letters from 'a' to 'z' for passwords of length 4 to 6. | No prior information about the password is available, and computational resources are abundant. |
Dictionary Attack |
Uses a pre-compiled list of common words, phrases, and passwords. | Trying passwords from a list like 'rockyou.txt' against a login form. | The target will likely use a weak or easily guessable password based on common patterns. |
Hybrid Attack |
Combines elements of simple brute force and dictionary attacks, often appending or prepending characters to dictionary words. | Adding numbers or special characters to the end of words from a dictionary list. | The target might use a slightly modified version of a common password. |
Credential Stuffing |
Leverages leaked credentials from one service to attempt access to other services, assuming users reuse passwords. | Using a list of usernames and passwords leaked from a data breach to try logging into various online accounts. | A large set of leaked credentials is available, and the target is suspected of reusing passwords across multiple services. |
Password Spraying |
Attempts a small set of commonly used passwords against a large number of usernames. | Trying passwords like 'password123' or 'qwerty' against all usernames in an organization. | Account lockout policies are in place, and the attacker aims to avoid detection by spreading attempts across multiple accounts. |
Rainbow Table Attack |
Uses pre-computed tables of password hashes to reverse hashes and recover plaintext passwords quickly. | Pre-computing hashes for all possible passwords of a certain length and character set, then comparing captured hashes against the table to find matches. | A large number of password hashes need to be cracked, and storage space for the rainbow tables is available. |
Reverse Brute Force |
Targets a single password against multiple usernames, often used in conjunction with credential stuffing attacks. | Using a leaked password from one service to try logging into multiple accounts with different usernames. | A strong suspicion exists that a particular password is being reused across multiple accounts. |
Distributed Brute Force |
Distributes the brute forcing workload across multiple computers or devices to accelerate the process. | Using a cluster of computers to perform a brute-force attack significantly increases the number of combinations that can be tried per second. | The target password or key is highly complex, and a single machine lacks the computational power to crack it within a reasonable timeframe. |
The Role of Brute Forcing in Penetration Testing
Penetration testing, or ethical hacking, is a proactive cybersecurity measure that simulates real-world attacks to identify and address vulnerabilities before malicious actors can exploit them. Brute forcing is a crucial tool in this process, particularly when assessing the resilience of password-based authentication mechanisms.
While penetration tests encompass a range of techniques, brute forcing is often strategically employed when:
Other avenues are exhausted: Initial attempts to gain access, such as exploiting known vulnerabilities or utilizing social engineering tactics, may prove unsuccessful. In such scenarios, brute forcing is a viable alternative to overcome password barriers.Password policies are weak: If the target system employs lax password policies, it increases the likelihood of users having weak or easily guessable passwords. Brute forcing can effectively expose these vulnerabilities.Specific accounts are targeted: In some instances, penetration testers may focus on compromising specific user accounts, such as those with elevated privileges. Brute forcing can be tailored to target these accounts directly.









