Summary
This module focuses on providing a detailed, guided simulation of a real penetration test, emphasizing the fine details of the penetration testing process.
In this module, we will cover:
- Entire Penetration Testing Process
- Pre-Engagement
- Information Gathering on Linux & Windows systems
- Assess gathered information for potential vulnerabilities
- Exploit vulnerabilities for initial access on Linux and Windows systems
- Escalate privileges
- Find and extract data from targets
- Explain note taking, Proof-of-Concept, documentation, and reporting
This module is broken down into sections with accompanying hands-on exercises to practice each of the tactics and techniques we cover. As you work through the module, you will see example commands and command output for the various topics introduced. It is worth reproducing as many of these examples as possible to reinforce further the concepts introduced in each section. You can do this in the target host provided in the interactive sections or your own virtual machine.
You can start and stop the module at any time and pick up where you left off. There is no time limit or "grading," but you must complete all of the exercises and the skills assessment to receive the maximum number of cubes and have this module marked as complete in any paths you have chosen.
The module is classified as "Easy" but assumes a working knowledge of the Linux command line and an understanding of information security fundamentals.
A firm grasp of the following modules can be considered prerequisites for successful completion of this module:
- Introduction to Information Security
- Introduction to Penetration Testing
Intro
In this module, we will see in practice how a penetration test could be conducted. We will go through each phase in detail so that you develop an understanding of why the individual components (discussed in Introduction to Information Security, Introduction to Penetration Testing, and Penetration Testing Process) exist and how they are interconnected. Furthermore, we want to illustrate the dependencies of these components and increase your understanding of how each one relates to the others .
Penetration Testing Recap
Penetration testing is an authorized simulation of a cyber attack, typically against an organization's network and it's subcomponents (such as web servers, mail servers, and applications). The purpose is to identify any security vulnerabilities that may exist within the client's IT systems, and fix them before a cybercriminal can take advantage. To accomplish this, the identified vulnerabilities are presented to the company in the form of a report, one which is designed to inform software developers, security teams, and administrators on how to best address the discovered issues.
Therefore, in this module, we will work through the entire process together so that you gain your first comprehensive experience with a penetration test. This hands-on approach will help you understand its requirements, how it works, what is needed to conduct one, and the benefits it provides to companies.
Penetration Testing Process
The penetration testing process consists of eight possible phases. Since these have already been explained in detail in the Penetration Testing Process module, here is just a brief summary of each phase:
-
Pre-Engagement: In this phase, everything necessary for the actual penetration test is discussed, developed, defined, and documented in writing. Here we obtain the necessary permissions and rights to execute hacking attacks on predetermined systems and simulate a real cyber attack. -
Information Gathering: In this phase, we collect as much information as possible about the target company to understand exactly how it is structured, how it functions, what it depends on, and what technical resources it requires. -
Vulnerability Assessment: After collecting as much information as possible, this must be carefully analyzed and correlated to identify potential attack vectors that could lead to a successful attack. -
Exploitation: Here, the identified attack vectors are targeted and defense mechanisms are bypassed. -
Post-Exploitation: Once we have gained access to a target system to control it from the inside and gathered enough internal information, we attempt to escalate privileges to the highest possible level. -
Lateral Movement: This phase occurs when we use the compromised system to move through the internal network. -
Proof-of-Concept: From all our notes, screenshots, and documentation, a report is created with the individual steps to reproduce our actions for successfully identifying each vulnerability. -
Post-Engagement: This is the phase where we show the report to the client and discuss it together, answer questions, and help them close the vulnerabilities found.
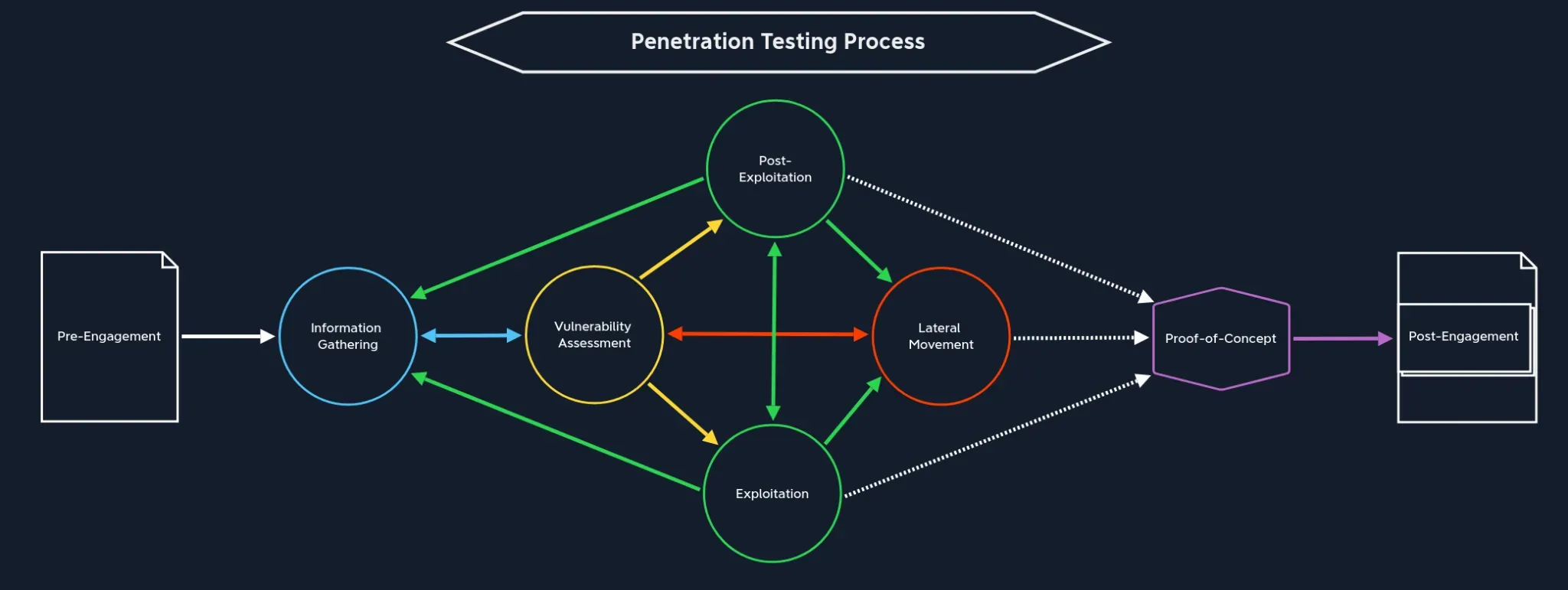
Throughout this module, we will work through all phases and highlight them explicitly. Use this representation to orient yourself during your penetration tests; similar to map which shows your current location, and where to go next. It often happens that we get stuck at a certain point and truly do not know how to process. This process will help you determine:
- if you haven't found something yet,
- if you don't know something yet,
- or if you're moving in the wrong direction.
Once you have gotten out of this "stuck" position, you'll realize that it is always one of these three points, and you can use this rule-of-thumb to make your own methodology faster and more effective.




