Summary
It is essential for future penetration testers to understand the structure of penetration testing, what it consists of, what it is for, how it is structured, what risks it entails and what responsibility it demands. With the knowledge provided, the student gains the necessary foundations to delve deeper into the actual penetration testing process and acquire the required practical skills. In this module, we will cover:
- the fundamentals of a penetration test
- types and domains of penetration tests
- compliance and ethics
- methodologies for different types of penetration testing
- profession
This module is broken down into sections with accompanying hands-on exercises to practice each of the tactics and techniques we cover.
You can start and stop the module at any time and pick up where you left off. There is no time limit or "grading," but you must complete all of the exercises and the skills assessment to receive the maximum number of cubes and have this module marked as complete in any paths you have chosen.
The module is classified as "FUNDAMENTAL" but assumes an understanding of information security fundamentals.
A firm grasp of the following modules can be considered prerequisites for successful completion of this module:
- Introduction to Information Security
Introduction
Penetration testing (pentesting), or ethical hacking, is where we legally mimic cyberattacks to spot security holes in a company's digital world. It's not just about finding weaknesses; it's about checking how well current security measures hold up, helping firms fix issues before the bad guys take advantage of the weaknesses. Penetration testers use real attack methods to test a system's defenses, pointing out where the security is lacking and suggesting ways to toughen it up. The whole deal involves planning, doing the test, and reporting back to manage risks smartly.
Take the MOVEit Transfer hack in 2023, where hackers nabbed data through file transfer systems. Proper pentesting might've caught this before it was too late. These tests can involve scanning networks, exploiting known issues, and seeing how far into a system an attacker could go. If standard tests don't cut it, we might switch to digging through code by hand or tricking people to find hidden weak spots.
Definition
A penetration test is a unique type of security assessment that goes beyond automated scanning and vulnerability identification. It involves attempting to exploit discovered vulnerabilities and gain unauthorized access, elevate privileges, or extract sensitive data. This approach allows organizations to understand not only what vulnerabilities exist in their infrastructure, but also how they could be leveraged and hardened in a real attack scenario, and what the impact would be.
Penetration tests are conducted by skilled security professionals, who are specialists in the field. Junior and senior specialists have a deep understanding of systems, networks, and offensive and defensive techniques. Those tests are carried out with the organization's full knowledge and permission, following strict rules of engagement and a defined scope.
Penetration testing encompasses a wide range of tasks, including:
- Reconnaissance
- Vulnerability Assessment
- Exploitation
- Post-exploitation
- Reporting
In a highly simplified illustration, we could imagine a penetration test proceeding in the following manner:
-
It starts with
reconnaissance(also known asinformation gathering), where testers gather information about the target organization, system or network, like scouting out a building before planning a break-in. -
Next, in the
vulnerability assessmentphase, they use tools to spot weak points, similar to checking for unlocked windows or doors. -
During the
exploitationphase, testers try to exploit those weaknesses to gain access or control over the system, just as a thief might test those unlocked doors. -
After that, in the
post-exploitationphase, they explore what else can be accessed, maintain control, and assess the impact of a successful attack, like seeing how far an intruder could roam inside a building. -
Finally, the
reportingphase documents everything: the vulnerabilities found, the risks they pose, and clear steps to fix them, so the system can be secured.
In the Penetration Testing Process module, the individual phases and the process are described in detail, but for now, we can focus on this simple illustration. The actual penetration testing process looks like following:
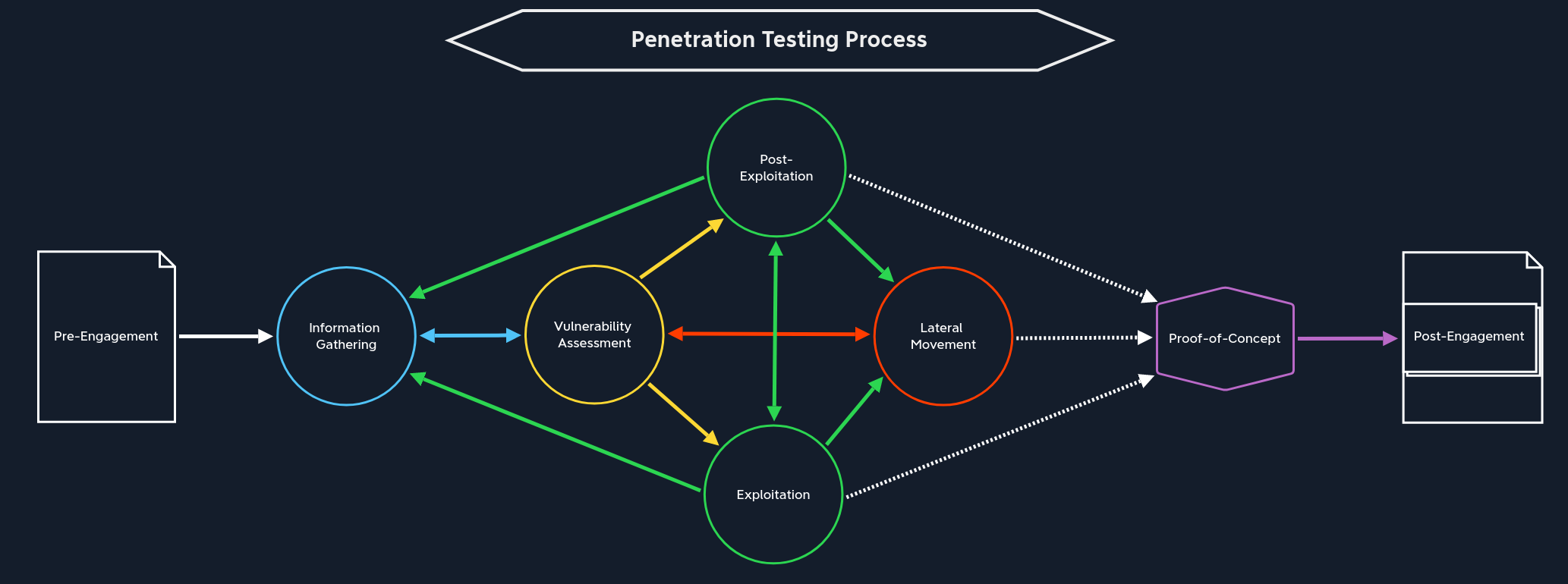
Companies use pentests to find and fix security holes before the bad unethical hackers do. With these tests we check if current defenses are up to the level they need to be in order to keep their systems and secrets safe. With our help, companies can fulfill compliance requirements, demonstrate their commitment to security, and maintain trust with their customers. This often involves adapting their strategies to address emerging threats and new attack methods. The cybersecurity landscape is moving and evolving very fast and this forward-thinking mindset enables organizations to recover more effectively from attacks and reduces the risk of costly data breaches.
Goals of Penetration Testing
The primary goals of penetration testing can be broken down into three categories:
- Evaluation of organization’s cyber security posture
- Testing organization’s defensive measures
- Operational & Financial impact risk assessment
In detail these categories consist of, but are not limited to:
-
Identifying Security Weaknesses: One of the fundamental goals of a pentest is to uncover vulnerabilities in systems, networks, or applications that could be exploited by attackers. This includes misconfigurations, software flaws, design weaknesses, and human-related vulnerabilities. -
Validating Security Controls: Penetration tests help organizations to assess the efficiency of their existing security measures and secure their digital assets. When we attempt to bypass these controls, we can determine if the security mechanisms in place are actually working as intended. -
Testing Detection and Response Capabilities: A pentest helps to identify if an organization has the necessary ability to detect and respond to security incidents. It helps identify gaps in monitoring systems, incident response procedures, and overall security awareness. -
Assessing Real-World Impact: By simulating real-world attack scenarios, we provide with the conducted penetration tests a realistic assessment of the potential impact of a successful breach. This includes understanding the extent of possible data loss, system compromise, or business disruption. -
Prioritizing Remediation Efforts: The results of a pentest can help organizations to prioritize their security efforts and allocate resources more effectively within the company. Critical vulnerabilities that pose the greatest risk can be addressed first. -
Compliance and Due Diligence: Regulatory frameworks require from companies frequent security checks like penetration tests and others. The reason for that is to ensure that organizations are actually safeguarding their critical information, customer data, and their systems. Performing these assessments it helps organizations to proof their commitment to due diligence in cybersecurity. -
Enhancing Security Awareness: Penetration tests often reveal security issues that may not be apparent through other means. They help to get the awareness about security risks among management, IT staff, and end-users. -
Verifying Patch Management: Pentests can verify whether security patches and updates have been properly applied and are effectively mitigating known vulnerabilities. -
Testing New Technologies: When new systems or applications are implemented within their internal or external infrastructure, penetration tests help the company to ensure that they are securely configured before being deployed in a production environment. -
Providing a Baseline for Security Improvements: The results of a pentest serve most of the time as a baseline for measuring security improvements over time. Subsequent tests can demonstrate progress in addressing identified issues.
Note: Pentesting is a powerful approach and is seen as a great tool for companies for analyzing and improving their overall security. It's important to remember that it provides just a snapshot of an organization's security measures at the specific point in time when the pentest has been conducted. Regular testing is mandatory to ensure a secure infrastructure environment and should be combined with ongoing security practices.
By achieving these goals, penetration testing enables organizations to take a proactive approach to security, identifying and addressing vulnerabilities before they can be exploited by malicious actors. This process not only enhances an organization's overall security posture but also provides valuable insights that can inform long-term security strategies and investments.




