Summary
Wi-Fi Protected Access 3 (WPA3) was introduced as the next-generation security standard to improve upon WPA2, promising stronger encryption, protection against offline dictionary attacks, and enhanced privacy for open networks. While WPA3 brings meaningful improvements such as Simultaneous Authentication of Equals, Opportunistic Wireless Encryption, and mandatory Protected Management Frames, it is not invulnerable. In this module, we will delve deeper into WPA3 OWE, SAE, and Enterprise networks (EAP-PWD), demonstrating various attack vectors and methods to compromise them.
In this module, we will cover:
- Introduction
- Attacks on OWE, such as:
- Evil Twin Attack
- Collider Evil Twin Attack
- Transition Mode Evil Twin
- Attacks on SAE, such as:
- Downgrade Attack
- Online Brute-Forcing
- Collider Evil Twin Attack
- Evil Twin Attack
- DOS Attacks
- WPA3 Enterprise Overview & Attacks
- Skills Assessment
This module is broken down into sections with accompanying hands-on exercises to practice each of the tools, tactics, and techniques we cover. There are no specific WiFi hardware requirements for this module, as Hack The Box manages all necessary resources. You will need to RDP into the provided attacker VM to perform the exercises.
As you work through the module, you will see example commands and command outputs for the various tools and topics introduced. Reproducing as many examples as possible is recommended to reinforce the concepts presented in each section.
You can start and stop the module at any time and pick up where you left off. There is no time limit or grading, but you must complete all of the exercises and the skills assessments to receive the maximum number of cubes and have this module marked as complete in any paths you have chosen.
This module is classified as "Medium" and assumes a working knowledge of Wi-Fi fundamentals, Linux systems and network fundamentals. A firm grasp of the following modules can be considered a prerequisite for the successful completion of this module:
Wi-Fi Protected Access 3 Overview
Over the years, weaknesses in legacy wireless security protocols like WEP, WPA, and WPA2 led to the need for a more resilient standard. Wi-Fi Protected Access 3 (WPA3) was developed to address these concerns and provide stronger protections in modern wireless environments. The protocol was introduced by the Wi-Fi Alliance following years of research and collaboration aimed at improving network security.
As with any new standard, however, WPA3 introduced its own set of challenges. Since its release, researchers such as Mathy Vanhoef and Eyal Ronen have uncovered several vulnerabilities in the protocol. Some of these can be exploited over-the-air without association, requiring a shift in how WPA3 networks are assessed and targeted compared to earlier generations.
WPA3 Authentication Methods
WPA3 authentication comes in three main types, each designed for different use cases.
WPA3-Open (OWE)WPA3-Personal (SAE)WPA3-Enterprise
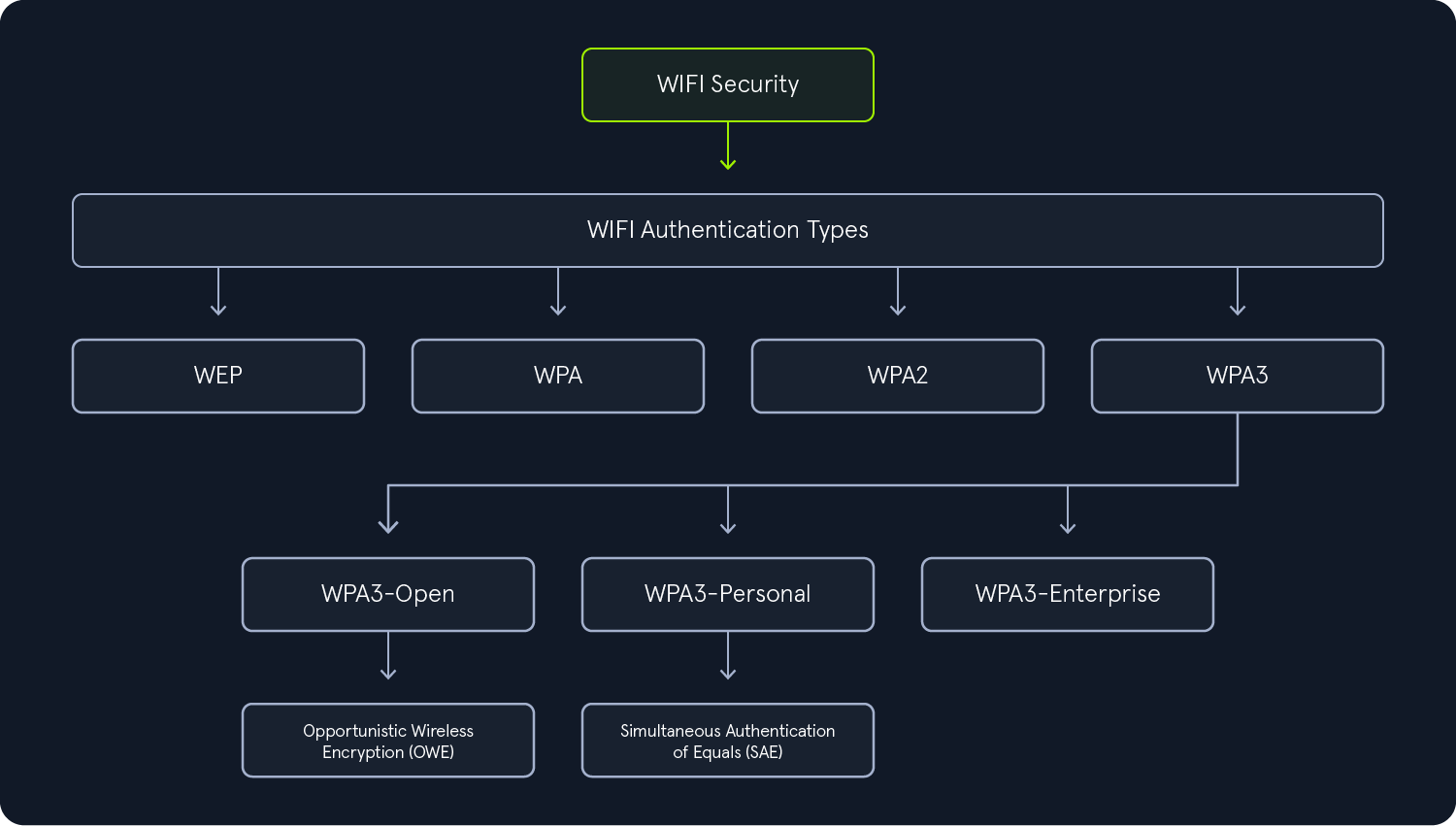
WPA3-OWE (Opportunistic Wireless Encryption) is a protocol introduced as part of the WPA3 standard. Aimed at improving the security of open Wi-Fi networks, it uses Diffie-Hellman key exchange to generate unique session keys and enables encrypted connections without requiring a password.
WPA3-SAE (WPA3-Personal) replaces WPA2's Pre-Shared Key (PSK) with a more secure handshake that's resistant offline attacks. It dynamically generates session-specifc encryption keys, preventing attackers from deriving passwords through captured data.
WPA3-Enterprise does not bring significant advancements for the enterprise sector, aside from an optional 192-bit security mode. In its mandatory configuration, it's essentially an extension of WPA2-Enterprise with the primary addition being support for Protected Management Frames (PMF). Beyond that, there are no major changes.
There are also different flavors of the main authentication types.
| Variant | Purpose | Backward Compatibility |
|---|---|---|
WPA3-Open (OWE) |
Provides encryption for open (passwordless) networks without authentication. | None |
WPA3-Open Transition Mode |
Allows clients without WPA3 support to still connect to open networks (unencrypted). | Legacy open (unencrypted) networks |
WPA3-Personal (SAE) |
Replaces WPA2-PSK with SAE for stronger password-based authentication. | None |
WPA3-Personal Transition Mode |
Enables WPA2-Personal (PSK) devices to connect while gradually moving to WPA3-SAE. | WPA2-Personal |
WPA3-Enterprise |
Provides stronger enterprise-grade security with 802.1X/EAP. | None |
WPA3-Enterprise Transition Mode |
Allows WPA2-Enterprise clients to connect alongside WPA3-Enterprise. | WPA2-Enterprise |
WPA3-Enterprise 192-bit Security Mode |
High-assurance mode using 192-bit cryptographic strength (for government/industry). | None |
As we delve into the various WPA3 attacks, these subcategories will be discussed in further detail.
The Backing Standards of WPA3
WPA3, including its enterprise variants, builds upon several IEEE standards to improve both security and performance. One key requirement is IEEE 802.11w, also known as Protected Management Frames (PMF), which helps prevent deauthentication and disassociation attacks by encrypting and authenticating management frames.
WPA3 networks can also incorporate optional roaming enhancements defined in IEEE 802.11k, 802.11v, and 802.11r, which aim to improve client handoffs between access points. These features aren't always enabled, but during reconnaissance, it's possible to detect their presence through beacon or probe response analysis
802.11k (Radio Resource Management): Provides clients with a list of neighboring APs for more efficient roaming decisions.802.11v (Power-Saving Features and BSS Transitions): Allows the network to manage client connections and suggest optimal APs.802.11r (Fast transition roaming): Speeds up authentication during handoffs, reducing delays and preventing connection drops, which are crucial for real-time applications like voice over Wi-Fi.
In the upcoming sections, we will explore the vulnerabilities in WPA3 implementations and the ways to exploit them. To be successful, however, it's important we understand WPA3's core mechanisms at a deeper level: OWE, SAE, and the Dragonfly handshake.