Summary
This module explores techniques for enumerating and attacking Wi-Fi networks through social engineering, focusing on evil twin attacks. We will cover methods for identifying access points, setting up rogue access points, configuring captive portals, and harvesting credentials using various tools. By understanding these attack vectors, we can better appreciate the importance of robust wireless security practices.
In this module, we will cover:
- Introduction
- Manual Evil Twin Attacks, such as:
- Evil Twin Attack on WPA2
- Karma & Mana Attacks
- Evil Twin Attack on WPA3
- Enteprise Evil Twin Attack
- Automated Evil Twin Attacks, using tools such as:
- Fluxion
- Airgeddon
- WifiPhisher
- EAPHammer
- MiTM Attacks, such as:
- DNS Spoofing
- Bypassing MFA using Evilginx
- SSL Interception
- Additional Attacks, such as:
- Using Flipper Zero
- Skills Assessment
This module is broken down into sections with accompanying hands-on exercises to practice each of the tools, tactics, and techniques we cover. There are no specific WiFi hardware requirements for this module, as Hack The Box manages all necessary resources. You will need to RDP into the provided attacker VM to perform the exercises.
As you work through the module, you will see example commands and command outputs for the various tools and topics introduced. Reproducing as many examples as possible is recommended to reinforce the concepts presented in each section.
You can start and stop the module at any time and pick up where you left off. There is no time limit or grading, but you must complete all of the exercises and the skills assessments to receive the maximum number of cubes and have this module marked as complete in any paths you have chosen.
This module is classified as "Medium" and assumes a working knowledge of Linux systems and network fundamentals. A firm grasp of the following modules can be considered a prerequisite for the successful completion of this module:
Introduction to Evil Twin Attacks
Rogue Access Point
A rogue access point is a wireless access point that imitates a legitimate one and is set up without the explicit authorization of the network administrator. It can be deployed either by a well-meaning employee or a malicious attacker, potentially posing significant security risks to the network.
Rogue access points can be categorized into two types:
Wired Rogue Access Points: These are unauthorized access points connected directly to the secure internal network, often posing a serious security threat as they provide a backdoor into the network.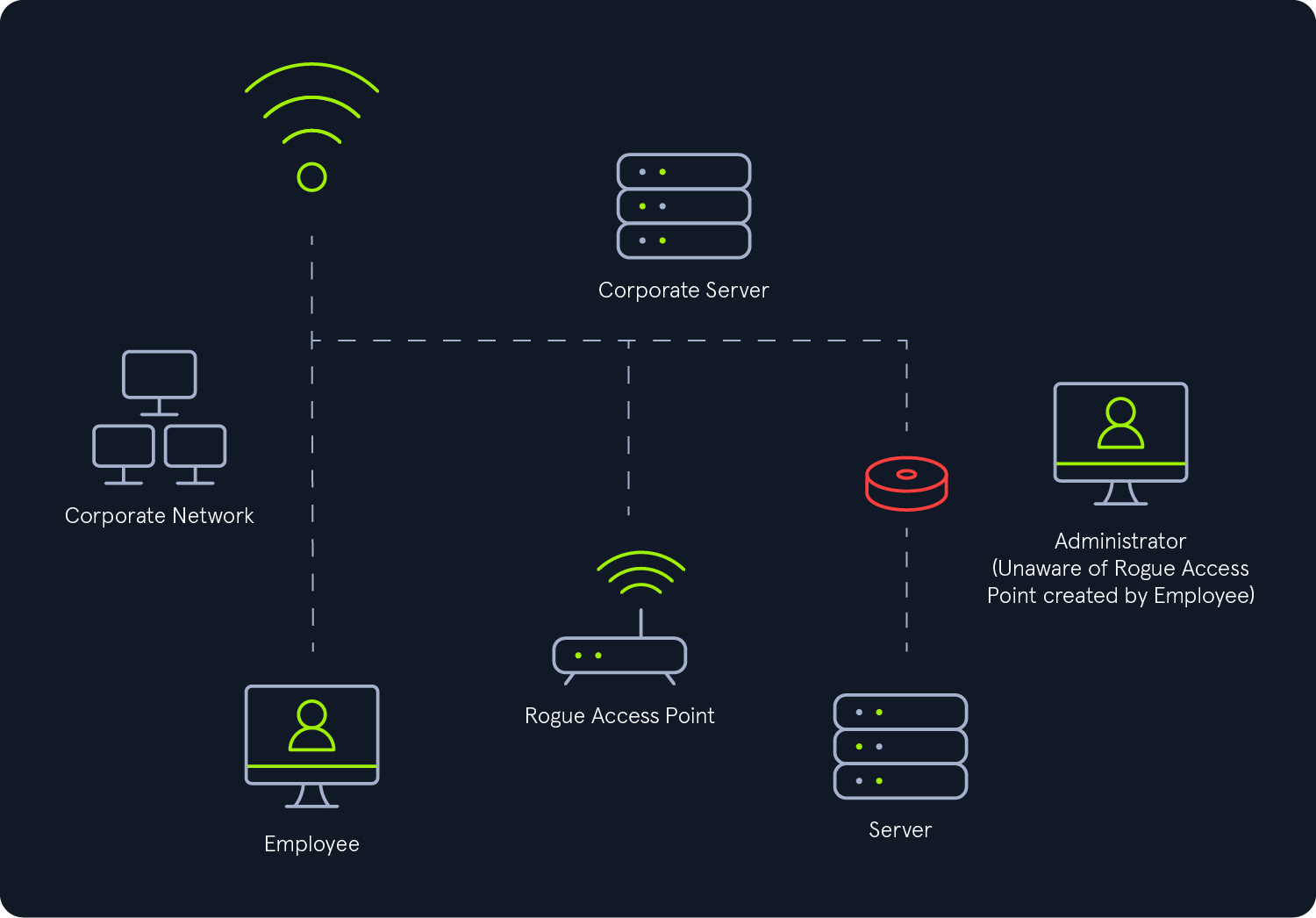
External Rogue Access Points: These are unauthorized access points not connected to the secure network. If one is found to be malicious or a potential risk—such as attracting or having already connected secure network wireless clients, it is classified as a rogue access point of the second kind, commonly referred to as an evil twin.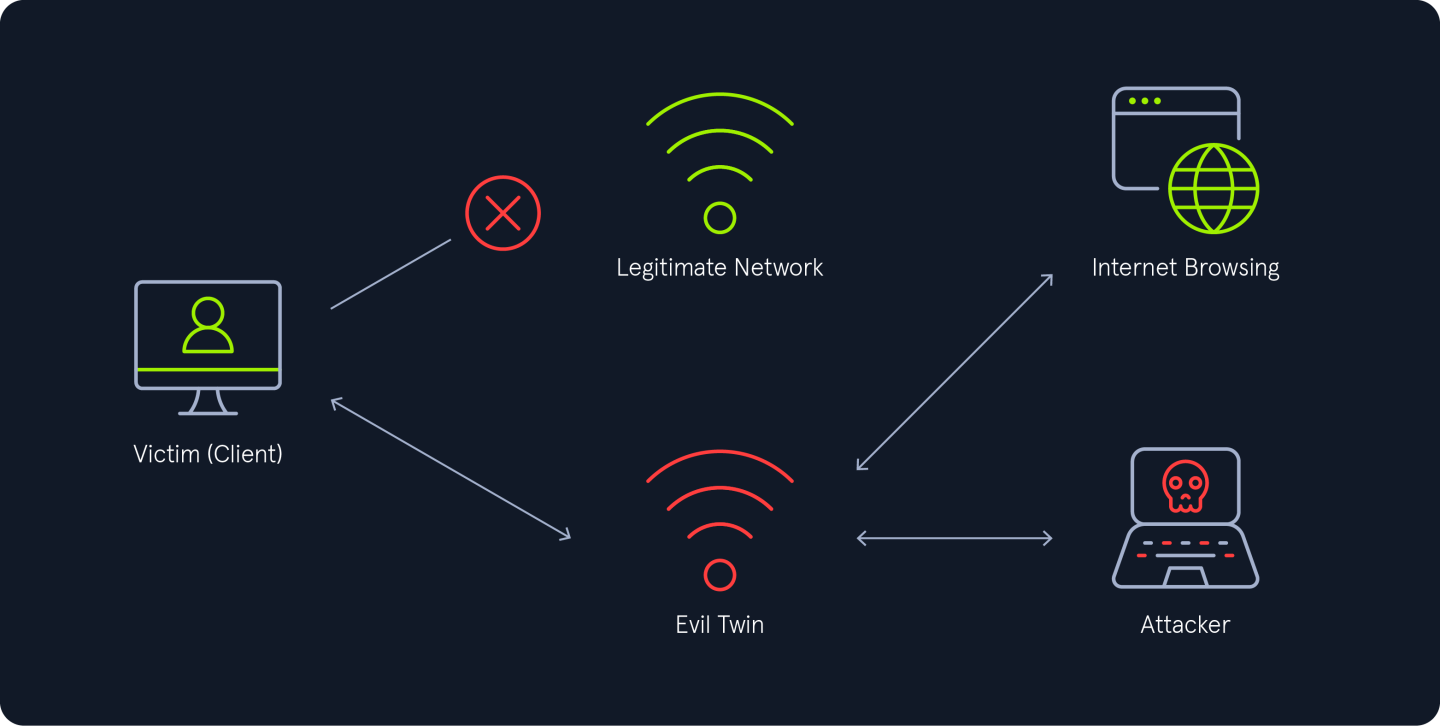
In this module, we will focus on the second type, the External Rogue Access Points , also known as the Evil Twin. For simplicity, we will use the terms rogue access point or fake access point interchangeably with evil twin throughout the module. We'll explore how to conduct evil twin attacks on WPA2, WPA3, and Enterprise networks, both manually and with automated tools. We'll dive into popular tools like Fluxion, Airgeddon, WiFi-Pumpkin3, WiFi-Phisher, and EAPHammer to perform these attacks. Additionally, we'll cover few MiTM (Man-in-the-Middle) techniques such as DNS spoofing, bypassing MFA with Evilginx2, and SSL interception. Finally, we'll demonstrate how to leverage the Flipper Zero device to create a rogue access point and host a captive portal to capture user credentials.
802.11 Roaming
The 802.11 protocol enables client devices (stations) to seamlessly roam between access points (APs) within the same Extended Service Set (ESS). However, the standard does not define specific criteria for selecting an AP when multiple options are available within the ESS. Typically, client devices are designed to choose the access point offering the best connection. This decision is usually based on factors such as signal strength, throughput, and signal-to-noise ratio. Similar to automatic network selection, client devices rely on the ESSID field in beacon frames to identify which nearby access points belong to their current ESS.
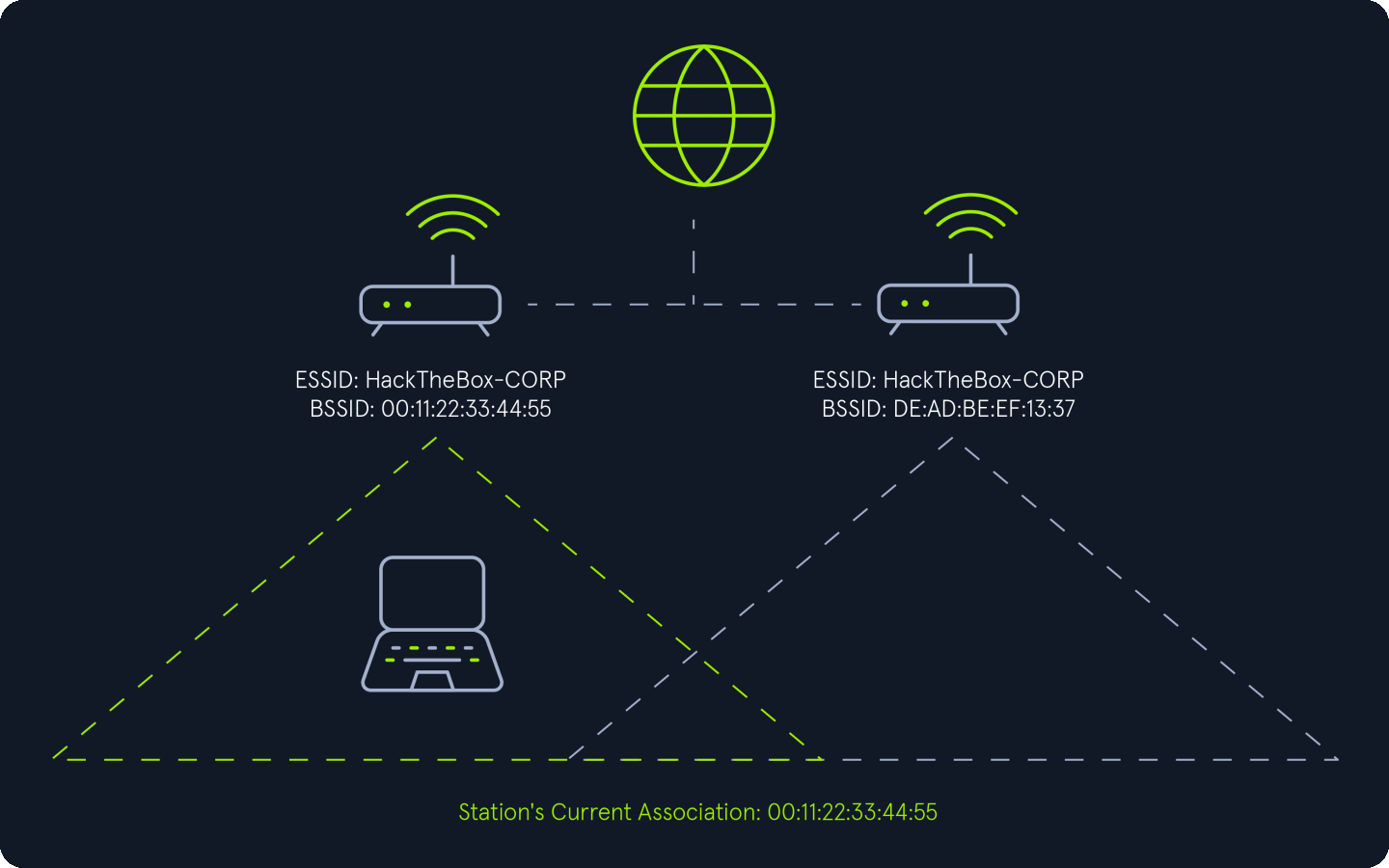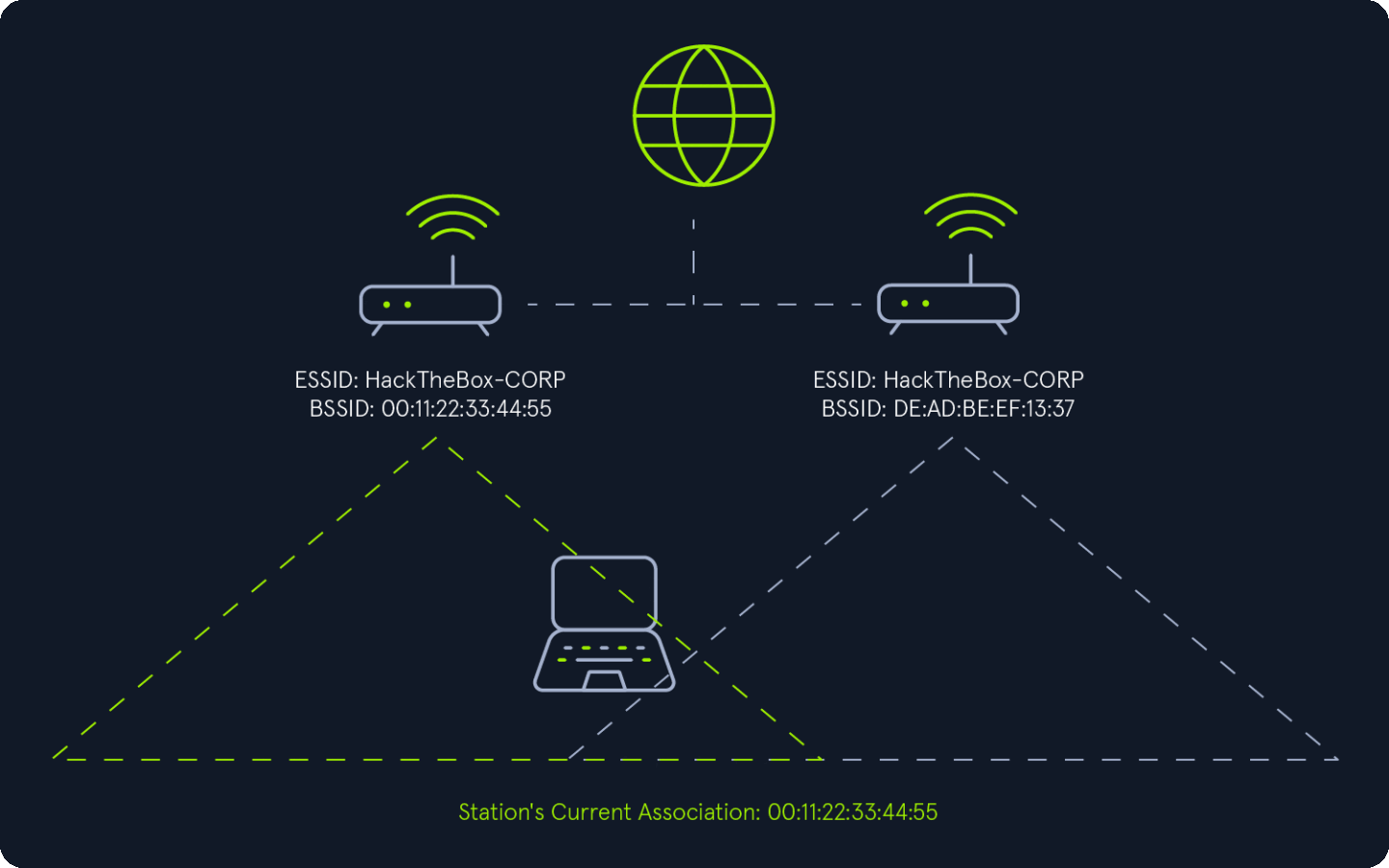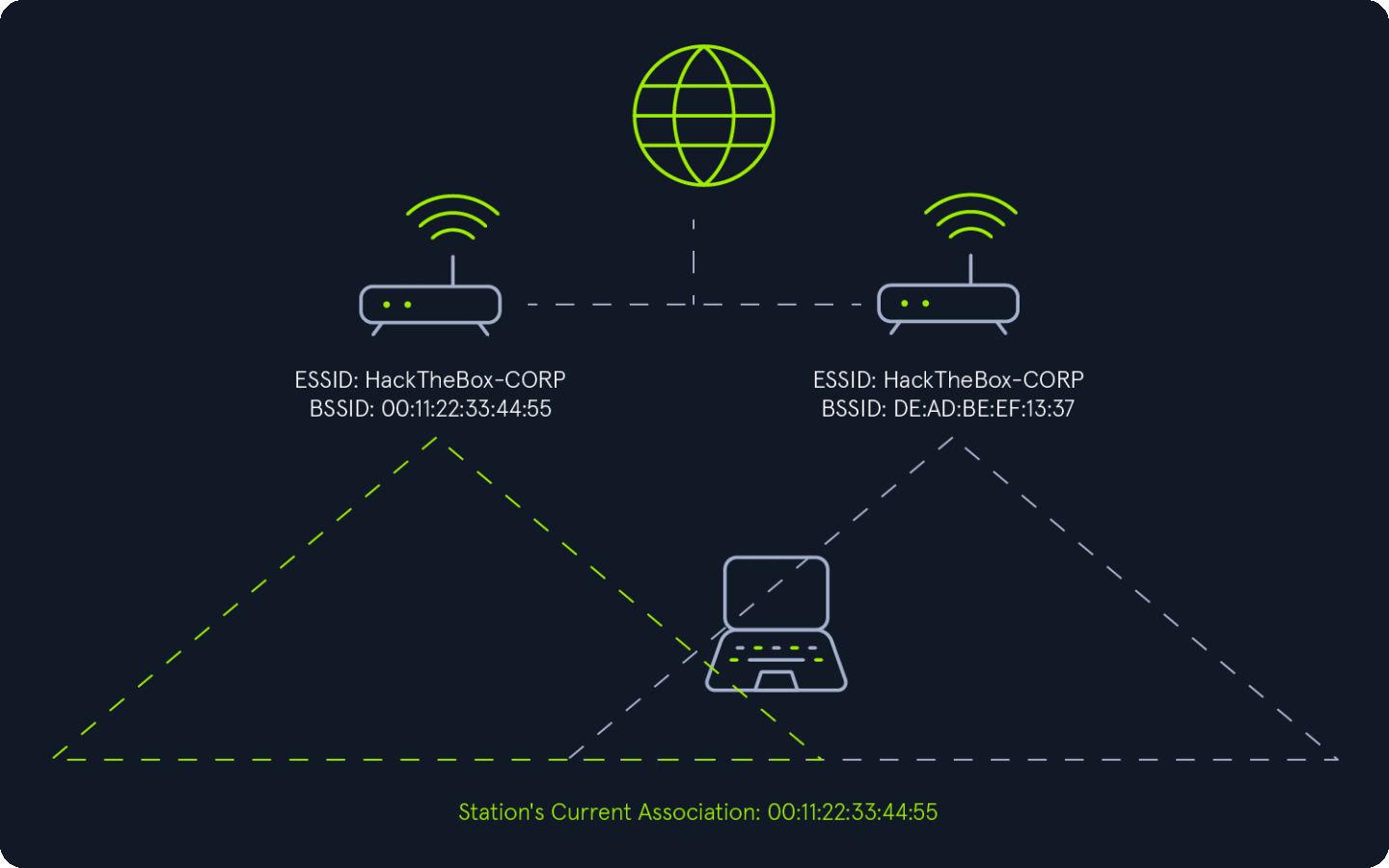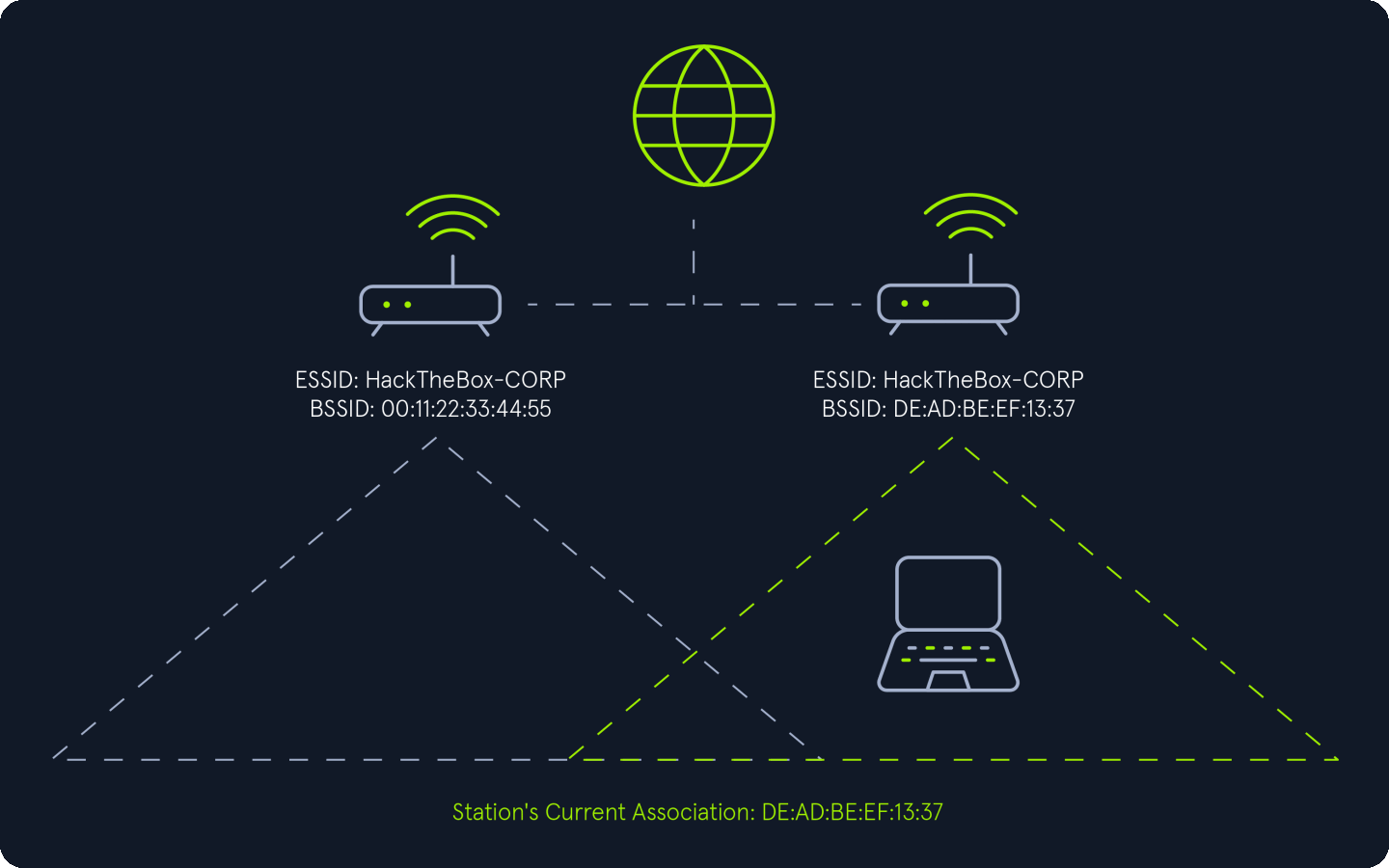
Abusing 802.11 Roaming
The 802.11 roaming process can be exploited by creating a rogue access point (AP) that uses the same ESSID as the target network. By offering a stronger signal than the legitimate access points, we can cause client devices connected to the target network to roam to our rogue AP. This can be achieved through one of two methods:
Enticement: Providing a stronger signal than the target access point to entice client devices to voluntarily connect to the rogue AP created by attacker.Coercion: Forcing client devices to disconnect from the target access point using techniques like deauthentication packets, jamming, or other denial-of-service (DoS) attacks. This compels the devices to roam to the rogue AP created by attacker.
Both methods allow an attacker to intercept and manipulate the communication of client devices as they connect to the rogue access point.
How Does an Evil Twin Attack Work?
Fake Access Point Setup: The attacker sets up a rogue access point (AP) mimicking the legitimate network by using the same SSID.Deauthentication and User Connection: The attacker broadcasts deauthentication packets to force clients off the real network, compelling them to reconnect to the open rogue AP.Traffic Monitoring and Captive Portals: Once connected to the rogue AP, the attacker may block internet access and redirect users to a fake captive portal. The captive portal mimics a legitimate login page, tricking users into providing their network credentials.
For WPA-PSK networks, evil twin attacks are generally more effective. The attacker typically begins by creating a rogue access point (AP) with the same name as the legitimate one but configured as an open network instead of using WPA2 authentication. To force clients to disconnect from the real AP, the attacker sends deauthentication packets, prompting users to manually select another Wi-Fi network. When clients connect to the rogue AP, their internet traffic is blocked, and users are redirected to a fake captive portal created by the attacker to steal their credentials.
WPA3 networks offer enhanced protection against deauthentication attacks due to the use of PMF (Protected Management Frames) protection. Even though an attacker can set up a rogue AP with the same name as the legitimate one and configure it as an open network, they cannot effectively perform deauthentication attacks to force client disconnections. However, evil twin attacks against WPA3 remain feasible through collision events that create Denial of Service (DoS) conditions. In this approach, the attacker creates a rogue AP with the same name (ESSID) and BSSID as the legitimate AP, configured with a fake password and WPA2 authentication using mana-loud (we'll cover the mana attack later). This setup creates a collision where clients are unable to connect to either AP, causing a denial-of-service condition. The attacker can then deploy an open rogue AP with the same name, enticing clients to connect and exposing them to potential credential theft.
Evil twin attacks on WPA Enterprise networks differ from those on WPA2 or WPA3 networks. Unlike PSK-based networks, where all users share a common passphrase, WPA Enterprise assigns each user unique credentials. To carry out the attack, an attacker sets up a rogue enterprise AP configured with a RADIUS server that accepts all authentication requests, regardless of validity. The rogue AP uses the same SSID as the legitimate one to trick users into connecting. When users connect using challenge-response methods such as CHAP, MSCHAP, or MSCHAPv2, their authentication hashes can be captured. These hashes can either be brute-forced locally to reveal the credentials or relayed in a PEAP attack to authenticate directly with the legitimate AP. If users connect using plain-text methods like GTC, their credentials are immediately exposed in clear text.
Next Steps
In the following sections we will do a deep dive into evil twin attacks, including:
- Evil Twin Attack on WPA2
- Karma & Mana Attacks
- Evil Twin Attack on WPA3
- Enterprise Evil Twin Attack
Each of these attacks is possible during real-world assessments so its important to be familiar with these and able to boast further knowledge. Developing a deeper understanding of these attacks not only enhances assessment capabilities but also strengthens defense strategies, ultimately boosting your expertise in wireless security assessments. In the next section, we will explore how to manually perform an evil twin attack against a WPA2 network.