Summary
Mobile devices hold sensitive personal and corporate information that hackers may want to obtain. Android Fundamentals seeks to provide a robust foundation in Android application security principles. It aims to enhance beginner penetration testers' understanding of how the Android platform and applications work and what steps they should follow to start with application penetration testing.
In this module, we will cover
- The architecture of the Android platform and its security features.
- The structure of the applications.
- The various application types and their development methods.
- The application's components and the ways they communicate.
- The testing environment, including emulated devices and tools.
- The methodology of performing application penetration testing.
This module is broken down into sections with accompanying hands-on exercises to practice each of the tactics and techniques we cover. As you work through the module, you will see example commands and command output for the various topics introduced. It is worth reproducing as many of these examples as possible to reinforce further the concepts introduced in each section. You can do this in the target host provided in the interactive sections or your own virtual machine.
You can start and stop the module at any time and pick up where you left off. There is no time limit or "grading," but you must complete all of the exercises and the skills assessment to receive the maximum number of cubes and have this module marked as complete in any paths you have chosen.
The module is classified as "Fundamental" but assumes a working knowledge of the Linux command line and an understanding of information security fundamentals.
Having a basic understanding of the modules listed below is sufficient for successfully completing this module:
While not necessary to complete the module, it is recommended that the learner have some familiarity with:
- Web Requests/Web Frameworks (HTML, CSS, JavaScript)
- Object Oriented Programming/working with IDE's
Additionally, students will require an Android Emulator to complete the lab exercises. The recommended emulation tool, Android Studio AVD, will likely need to be installed on the learner's host machine (due to issues with nested virtualization within the Pwnbox.) Whichever method you choose, we are certain you will enjoy this deep dive into the world of Android.
About Android
Android is a mobile operating system created for touchscreen devices like phones and tablets. Based on a modified version of the Linux Kernel, it was developed by the Open Handset Alliance consortium and commercially sponsored by Google. Most Android devices come pre-installed with Google Mobile Services (GMS), a proprietary software suite that includes apps like Google Play and Google Chrome. Google collaborates with various vendors, such as Samsung and HTC, to allow customization of user interfaces and software features. Beyond smartphones and tablets, Android OS is also used in smart TVs and wearables developed by Google. Android applications are distributed through various app stores, including Google Play Store, Amazon Appstore, Samsung Galaxy Store, Huawei AppGallery, and open-source platforms such as Aptoide, F-Droid, APKPure, and APKMirror.
History
In October 2003, Andy Rubin, Rich Miner, Nick Sears, and Chris White founded Android Incorporated in Palo Alto, California. In 2005, after Rubin's efforts to attract investors, Google acquired the company for the reported price of around $50 million. After some time, Rubin's team at Google developed the first mobile device powered by the Linux kernel. In 2007, an early prototype with no touchscreen and a physical QWERTY keyboard was created, followed by the HTC Dream (also known as T-Mobile G1, the first commercial Android device released in September 2008.) Android's major releases before version 10 were named after desserts. For example, the first Android versions were called Cupcake, Donut, Eclair, and Froyo.
In 2010, Google launched the Nexus series, and in May 2013, it announced a special version of the Samsung Galaxy S4 that included Google Play, followed by the HTC One Google Play edition and the Moto G Google Play edition. In June 2014, Google introduced Android One, a program aimed at enabling third-party manufacturers to produce high-quality smartphones easily and at low cost. In October 2016, Google replaced the Nexus series with the Pixel and Pixel XL smartphones, the first phones designed and marketed entirely by Google. On September 3, 2019, Google released Android 10 (initially referred to as Android Q) for Pixel devices, officially ending the tradition of naming major Android versions after desserts.
Versions
Below is a table showing the correlation between Android codenames, versions, API levels, and release dates.
| Name | Version | API Level | Release Date |
|---|---|---|---|
| Android 1.0 | 1.0 | 1 | September 23, 2008 |
| Android 1.1 | 1.1 | 2 | February 9, 2009 |
| Android Cupcake | 1.5 | 3 | April 27, 2009 |
| Android Donut | 1.6 | 4 | September 15, 2009 |
| Android Eclair | 2.0 | 5 | October 27, 2009 |
| Android Eclair | 2.0.1 | 6 | December 3, 2009 |
| Android Eclair | 2.1 | 7 | January 11, 2010 |
| Android Froyo | 2.2 – 2.2.3 | 8 | May 20, 2010 |
| Android Gingerbread | 2.3 – 2.3.2 | 9 | December 6, 2010 |
| Android Gingerbread | 2.3.3 – 2.3.7 | 10 | February 9, 2011 |
| Android Honeycomb | 3.0 | 11 | February 22, 2011 |
| Android Honeycomb | 3.1 | 12 | May 10, 2011 |
| Android Honeycomb | 3.2 – 3.2.6 | 13 | July 15, 2011 |
| Android Ice Cream Sandwich | 4.0 – 4.0.2 | 14 | October 18, 2011 |
| Android Ice Cream Sandwich | 4.0.3 – 4.0.4 | 15 | December 16, 2011 |
| Android Jelly Bean | 4.1 – 4.1.2 | 16 | July 9, 2012 |
| Android Jelly Bean | 4.2 – 4.2.2 | 17 | November 13, 2012 |
| Android Jelly Bean | test | 18 | July 24, 2013 |
| Android KitKat | 4.4 – 4.4.4 | 19 | October 31, 2013 |
| Android KitKat | 4.4W – 4.4W.2 | 20 | June 25, 2014 |
| Android Lollipop | 5.0 – 5.0.2 | 21 | November 4, 2014 |
| Android Lollipop | 5.1 – 5.1.1 | 22 | March 2, 2015 |
| Android Marshmallow | 6.0 – 6.0.1 | 23 | October 2, 2015 |
| Android Nougat | 7.0 | 24 | August 22, 2016 |
| Android Nougat | 7.1 – 7.1.2 | 25 | October 4, 2016 |
| Android Oreo | 8.0 | 26 | August 21, 2017 |
| Android Oreo | 8.1 | 27 | December 5, 2017 |
| Android Pie | 9 | 28 | August 6, 2018 |
| Android 10 | 10 | 29 | September 3, 2019 |
| Android 11 | 11 | 30 | September 8, 2020 |
| Android 12 | 12 | 31 | October 4, 2021 |
| Android 12L | 12.1 | 32 | March 7, 2022 |
| Android 13 | 13 | 33 | August 15, 2022 |
| Android 14 | 14 | 34 | October 4, 2023 |
| Android 15 | 15 | 35 | September 3, 2024 |
| Android 16 | 16 Beta | 36 | March 13, 2025 |
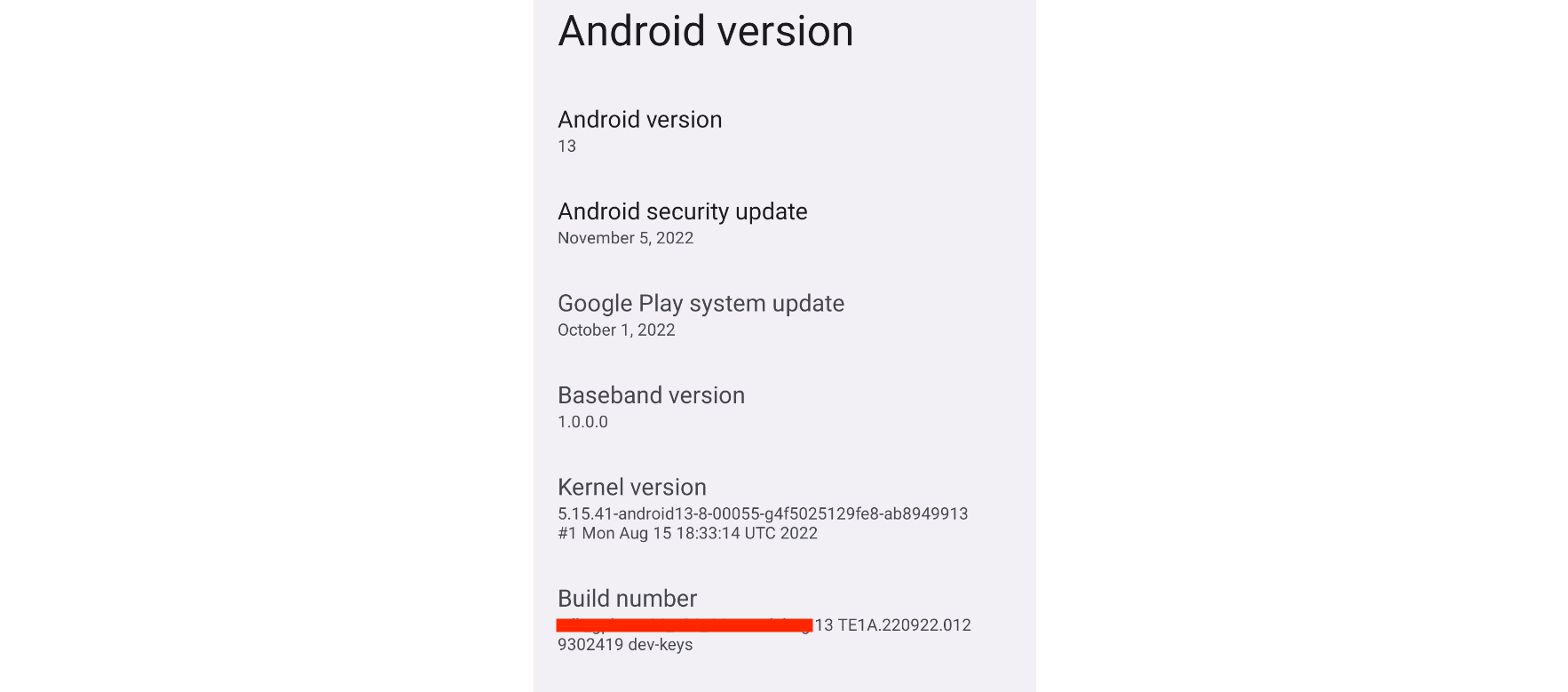
The Android version of the device, along with other information, can be found under Settings -> About emulated device -> Android version.
Hardware
Although Android supports a range of hardware architectures, the majority of devices use the ARM (AArch64) architecture. Architectures such as x86 and x86-64 have also been supported, primarily in later Android versions that included Intel processors. The unofficial project Android-x86 provided support for the x86 architecture even before it was officially supported by Android. Non-native architectures like x86 can also run on the Android Emulator included with the SDK, as well as on various third-party emulators. Android devices typically include a variety of hardware components, such as video cameras, GPS, orientation sensors, dedicated gaming controls, accelerometers, gyroscopes, barometers, magnetometers, proximity sensors, pressure sensors, thermometers, and touchscreens. Moving on to the next section, we will discuss the main components of the Android operating system and their attributes.





