Summary
This module is intended for students looking to gain an introduction and hands-on experience designing and implementing API hooks using different techniques and libraries, such as inline patching and Microsoft's Detours. It covers how APIs like CreateFileA, WriteFile, etc., can be intercepted, how parameters and return values can be logged, and how processes can be injected with custom DLLs for runtime monitoring.
By the end of this module, you will be able to understand following concepts:
-
How an API Executes in Windows OS: Understand the flow of a function call from user-mode application code to the operating system’s kernel, including module loading and execution flow. -
Import Address Table (IAT) Hooking: Learn how to manipulate the Import Address Table to redirect API calls by replacing function addresses at process load time. -
Inline Hooking and Using Microsoft Detours: Explore the technique of modifying function prologues at runtime and how Microsoft’s Detours library simplifies safe and atomic function patching. -
Kernel Driver for API Monitoring: Discover how kernel-mode drivers can be used to intercept and monitor API calls at a lower privilege level for advanced debugging. -
EDR Driver Development and Deployment: Basics of Endpoint Detection and Response (EDR) driver(s) that hooks, filters, and analyzes API usage across processes for security monitoring. -
Introduction to API Calls Detection: Learn the fundamentals of detecting suspicious or malicious API calls by tracking execution patterns, parameters, and system interactions. -
API Calls in Token Impersonation/Theft: Explains how adversaries misuse API calls to impersonate or steal tokens, bypass authentication, and elevate privileges. -
Create Process with Token: Understand how adversaries use token-based process creation to launch processes with elevated or unauthorized privileges. -
Hooking DLL to Detect Access Token Attacks: Implement DLL injection and API hooking techniques to monitor and log access token manipulation attempts in real-time. -
Log Windows API Calls with Parameters: Learn how to capture and log detailed information about API calls, including function arguments and system state at the time of execution. -
Implementation of an API Logger: The process of designing and coding a simple API logger that hooks functions, records data, and outputs logs for analysis. -
API Logging Demo with Return Values: See practical demonstrations of API hooking where both input parameters and return values are logged to provide comprehensive visibility into process behavior.
This module also contains a Skills Assessment exercise based on Splunk, where the participants will run queries to find the answer.
The following prerequisites are highly recommended in order to easily follow this module:
- Completion of Intro to Assembly Language.
- Completion of Process Injection Attacks and Detection.
- Completion of Understanding Log Sources & Investigating with Splunk.
- Completion of Detecting Windows Attacks with Splunk.
- Foundatational knowledge of C/C++, structures, and pointers.
Introduction to API Monitoring
While Windows Event Logs are vital for security monitoring and detection, there are still cases where adversarial activity doesn’t produce any relevant events. For example, access token manipulation using APIs like DuplicateToken or DuplicateTokenEx may occur without generating alerts in standard event logs. Or, let's say a process is trying to use the ReadProcessMemory() API to read the memory of some critical or sensitive process. In such scenarios, relying solely on log-based detection is insufficient, and deeper visibility into process behavior becomes necessary.
This is where Windows API monitoring comes into play. Monitoring API execution allows defenders, analysts, and developers to observe how processes interact with system resources at runtime - something that’s not new but remains useful. In fact, many antivirus and endpoint protection solutions have been leveraging API hooks for decades to detect malicious actions that bypass traditional defenses. Unlike log aggregation or file-based monitoring, API monitoring provides real-time insight into the operations carried out by applications, such as opening files, modifying registry entries, allocating memory, or spawning processes. It’s especially useful in detecting sophisticated threats like process hollowing, token theft, DLL injection, and privilege escalation, where adversaries operate beneath the radar of conventional monitoring solutions.
The diagram below shows an example where API hooking is used to inspect the API parameters and take necessary action (e.g., terminate the process) if something suspicious is found. If the checks are passed, then the API call is forwarded to the original function.
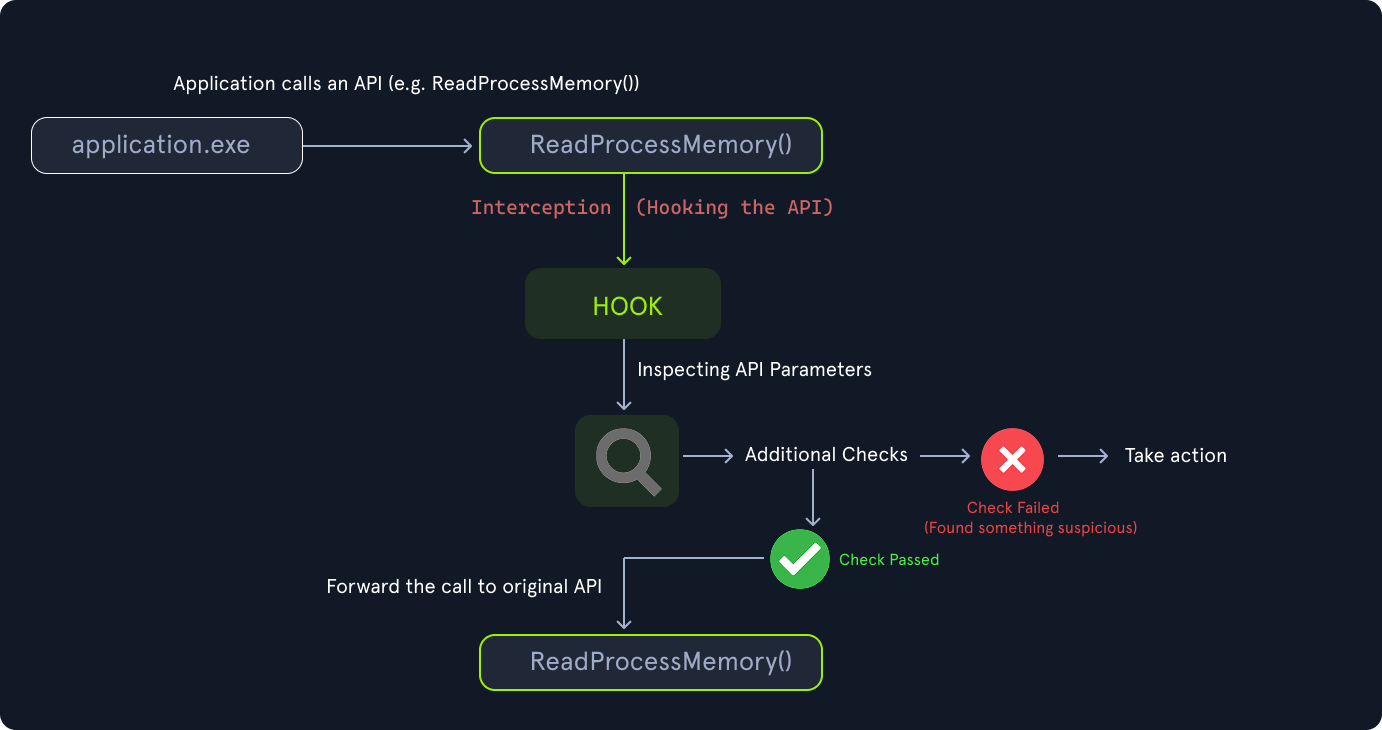
In this course, we’ll go beyond theory and explore how API monitoring is implemented in practice. We’ll discuss hooking techniques such as Import Address Table (IAT) patching (hooking), Inline Hooking using libraries like Microsoft Detours, and Kernel-mode monitoring. We’ll walk through scenarios where API monitoring is useful, such as tracking how malware manipulates tokens.
API Monitoring Techniques
There are many techniques for monitoring API calls in Windows, such as:
-
Import Address Table (IAT) Hooking:- Modifies API addresses in the executable’s import table.
- Effective when APIs are resolved at load time.
-
Inline Hooking:- Overwrites the first few bytes of the API’s implementation.
- Redirects execution to a monitoring function.
- Useful for real-time tracking but requires careful memory management.
-
Export Address Table (EAT) Hooking:- Targets dynamically resolved APIs by intercepting their entry points in the export table.
-
Kernel-mode monitoring:- Hooks system calls at a lower privilege level.
- Provides broader coverage and access to protected resources.
-
Using Hooking Libraries (e.g., Microsoft Detours):- Simplifies hook installation and management.
- Ensures atomic updates and reduces risks of instability.
In the next sections, we'll dive deep into different API monitoring and hooking techniques.
